EFF: How Tor Works
Purpose:
Tor is software that directs Internet traffic through a network of relay servers in order to conceal the source and destination of the traffic. It allows for the anonymous sharing of information over the Internet, and can be used to circumvent Internet censorship (TOR01). Tor also enables the creation of hidden services, which hide the locations of people who publish content or run servers (TOR02).
Tor can be used by software developers to create new communication tools with built-in privacy features (TOR01).
Capabilities:
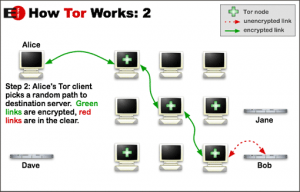
- Onion routing – A technique for concealing the source and destination of network traffic by encrypting it and forwarding it through a series of relays. Each relay decrypts a layer of encryption to reveal the address of the next relay and passes the remaining encrypted data on to it. The final relay, known as the exit node, decrypts the innermost layer of encryption and sends the original data to its destination without revealing, or knowing, the address of the source. Because no single relay knows both the source and destination of the traffic, this method eliminates any single point at which the communication can be de-anonymised through network surveillance (DIN01).
- Hidden service – A service that is only accessible via the Tor network. The clients connecting to a hidden service cannot discover its location or vice versa. Hidden services use domain names ending with the ‘.onion’ suffix.
Surveillance mitigation:
- Traffic analysis – Can be used to infer who is talking to whom over a public network. Knowing the source and destination of a person’s Internet traffic makes it possible to track their behaviour and interests (TOR01).
- Anonymity – Onion routing separates identification from routing so that information can be published and accessed anonymously.
Vulnerabilities:
- Traffic confirmation – Tor cannot protect against the monitoring of traffic at the boundaries of the Tor network (TOR03). An observer who can monitor traffic entering and exiting the Tor network may be able to determine who is communicating with whom, even if the traffic is encrypted end-to-end.
- Exit node blocking – Administrators of Internet sites can prevent their sites from being accessed via the Tor network, or offer reduced functionality to Tor users (TOR04).
- Exit node eavesdropping – Tor cannot encrypt the traffic between exit nodes and Internet sites. This means that an exit node can capture or modify any traffic passing through it that does not use end-to-end encryption. For example, in 2007, a security researcher intercepted thousands of private email messages sent by embassies and human rights groups around the world by monitoring the traffic of an exit node he was running (TAI01).
- Application layer information leaks – Certain applications leak identifying information at the application layer even when they are used over Tor (MAN01).
Layers of operation:
- Transport layer: Tor provides an anonymous transport layer that can be used by other applications.
- Application layer: Tor relays communicate across the Internet at the application layer.
Background:
Tor is a volunteer network of computers, known as relays or nodes. These nodes receive traffic and forward it to other nodes so that it will eventually go to its final destination. Tor can be used to browse the web anonymously using the Tor Browser, a modified version of the Mozilla Firefox web browser. Opening the browser automatically connects to the Tor network (EFF01). The network is used by a variety of people who want to maintain their anonymity. It is regularly used by journalists, activists and whistleblowers (TOR05).
The NSA attacked the Tor network through its programme EGOTISTICAL GIRAFFE (GUA01). The programme exploited a bug in the web browser to de-anonymise Tor users (MOZ01, SCH01). The bug has since been fixed.
Sources:
Electronic Frontier Foundation (EFF)
1) https://www.eff.org/torchallenge/what-is-tor.html
Guardian (GUA)
1) http://www.theguardian.com/world/interactive/2013/oct/04/egotistical-giraffe-nsa-tor-document
Dingledine, R., Mathewson, N., Syverson, P. (DIN)
1) Tor: The Second-Generation Onion Router. 2004. https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf
Manils, P., Abdelberri, C., Le Blond, S., Kaafar, M., Castelluccia, C., Legout, A., Dabbous, W. (MAN)
1) Compromising Tor Anonymity Exploiting P2P Information Leakage. 2010. http://cryptome.org/2013/04/tor-p2p-compromise.pdf
Mozilla (MOZ)
1) https://blog.mozilla.org/jorendorff/2013/12/06/how-egotisticalgiraffe-was-fixed/
Schneier on Security (SCH)
1) https://www.schneier.com/blog/archives/2013/10/how_the_nsa_att.html
TAILS (TAI)
1)https://tails.boum.org/doc/about/warning/index.en.html
Tor Project (TOR)
1) https://www.torproject.org/about/overview.html.en
2) https://www.torproject.org/docs/hidden-services.html.en
3) https://blog.torproject.org/category/tags/traffic-confirmation
4) https://www.torproject.org/docs/faq-abuse.html
5) https://www.torproject.org/about/torusers.html.en
